Quantum Vulnerability in Bitcoin: A Manageable Risk
Quantum Vulnerability in Bitcoin: A Manageable Risk
The headline hits the screens like a digital shockwave: “Quantum Supremacy Achieved.” Instantly, the minds of Bitcoin maximalists and long-term crypto holders race. Will the very foundation of Satoshi’s creation—cryptographic security—crumble under the immense power of future quantum computers? For years, this has been the ultimate 'Black Swan' event for the digital economy.
But veteran cybersecurity experts and protocol developers have a different take. The threat is real, yes, but the narrative often leans too heavily into doomsday scenarios. While large-scale, fault-tolerant quantum computing promises an unprecedented challenge to classical encryption, the risk to the Bitcoin network today is not catastrophic, nor is it insurmountable. It is, in fact, highly manageable.
This trending update cuts through the fear, uncertainty, and doubt (FUD) to deliver a clear-eyed assessment of the quantum threat landscape. We explore precisely where the vulnerabilities lie, and more importantly, the strategic countermeasures already being implemented by the crypto community.
Deconstructing the Quantum Threat: Shor's Algorithm vs. ECC
To understand the danger, we must first understand Bitcoin’s core defense mechanism: Elliptic Curve Digital Signature Algorithm (ECDSA). This highly secure math allows users to prove ownership of funds (using their private key) without ever revealing that key. This process is known as public key cryptography.
Today’s computers rely on the difficulty of solving the underlying mathematical problem: factoring large prime numbers. This is computationally intensive—a task that would take classical supercomputers millennia to complete. However, this barrier is precisely what a powerful quantum computer, armed with **Shor's Algorithm**, is designed to bypass.
Shor's Algorithm provides a mechanism for exponentially speeding up the factoring process. Applied to Bitcoin, this means a quantum computer could potentially take a user’s public key—which is broadcast to the network when a transaction is made—and rapidly deduce the corresponding private key. Once the private key is known, the attacker has complete control over those funds.
It is important to note the difference between Shor's Algorithm and **Grover's Algorithm**. While Shor's targets the asymmetric key cryptography (the foundation of Bitcoin security), Grover's Algorithm offers a quadratic speedup for searching databases. While useful, Grover's impact is significantly less severe than Shor's when considering the wholesale cracking of private keys. The primary existential threat comes from the factoring capabilities of Shor’s.
The timeline for this capability—known as the "crypto-apocalypse date"—is hotly debated, but most experts agree we have at least a decade, possibly longer, before cryptographically relevant quantum computers (CRQCs) become widely available. This timeline is crucial; it gives developers room to maneuver.
The threat is fundamentally tied to the ability to transition from the public key (P) back to the private key (K). If P is never revealed, K remains secure.
Identifying the Real Risk Vectors: The Vulnerable Wallets
The "manageable risk" thesis hinges on a critical detail: not all Bitcoin is equally vulnerable. The risk level is determined by how, and when, an address’s public key is exposed on the blockchain.
We can categorize Bitcoin holdings into two major risk groups:
1. High-Risk: Address Reuse and Legacy P2PKH
The most immediate and critical vulnerability lies in older address formats, specifically Pay-to-Public-Key-Hash (P2PKH) addresses, which often start with a ‘1’. These addresses inherently reveal their public key as soon as the associated funds are spent (i.e., when the transaction is signed and broadcast).
Crucially, high risk is compounded by **address reuse**. If a user sends a small amount of BTC from a P2PKH address, the remaining balance (the unspent transaction output, or UTXO) is now linked to a public key already visible on the blockchain. This exposed public key is immediately susceptible to harvesting by quantum attackers.
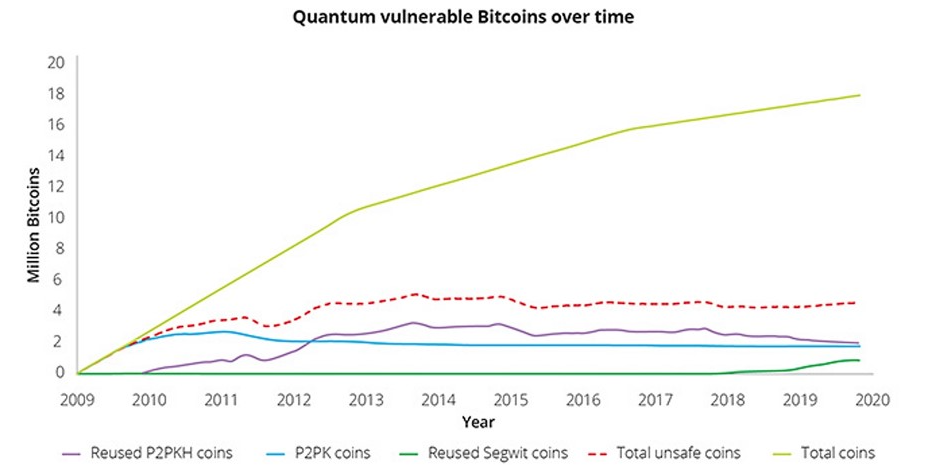
Millions of Bitcoins currently sit in P2PKH addresses that have been used to send funds at least once. These funds represent the "low-hanging fruit" for future quantum attacks. While they are safe *today*, as soon as a CRQC becomes operational, these exposed keys will be the first targets.
- Risk Factor A: Public key is visible on-chain.
- Risk Factor B: Funds are still sitting at that public address.
- Mitigation Needed: Move these funds to a new, non-reused, non-exposed address immediately.
2. Low-Risk: SegWit, Taproot, and Hardware Wallets
Modern Bitcoin addresses—such as SegWit (starting with ‘3’ or ‘bc1’) and the latest Taproot addresses (starting with ‘bc1p’)—offer an inherent layer of quantum defense, though this is often misunderstood.
These formats use scripts that hash the public key (or the script) before it is broadcast. For these addresses, the public key is typically only fully revealed *after* the funds are spent, and sometimes not even then (as in the case of complex Taproot scripts).
For funds sitting securely in an unspent, modern SegWit or Taproot UTXO, the quantum attacker has nothing to target. They cannot apply Shor’s Algorithm without first having the target public key. Until the owner decides to move those funds, they remain cryptographically hidden.
Furthermore, the physical security offered by modern **hardware wallets** adds another critical layer. These devices keep the private key completely isolated from any internet connection, ensuring that even if the public key is revealed during a spend, the physical device must still be accessed and authorized to move the remaining funds.
The Path Forward: Mitigation and Post-Quantum Solutions
The quantum threat is not a technological cliff edge, but a sloping hill that the Bitcoin protocol can ascend through planned upgrades. The community is not idle; research and implementation strategies are moving forward on two fronts: immediate user mitigation and long-term protocol hard-forks.
Immediate User Mitigation Strategy
For every Bitcoin holder, the following steps minimize current and future quantum exposure:
- Move Legacy Funds: If you hold Bitcoin in any P2PKH address (starting with ‘1’) that has ever been used to spend funds, transfer the remaining balance to a new, fresh address.
- Avoid Address Reuse: Never send funds back to a previously used address. This practice is poor security hygiene regardless of the quantum threat, but it is fatal in a quantum landscape.
- Utilize Modern Addresses: Default to using native SegWit (bech32) or Taproot addresses, as these delay the exposure of the public key until the transaction is confirmed, or beyond.
- Secure Keys Offline: Use high-quality hardware wallets. The gap between the time a public key is broadcast and when the transaction is confirmed is the quantum attacker's window. Keeping the private key locked down is paramount.
The Long-Term Solution: Post-Quantum Cryptography (PQC)
The ultimate fix involves upgrading the Bitcoin protocol’s signature scheme itself, migrating away from ECDSA to algorithms that are provably resistant to Shor’s and Grover’s algorithms. This field is known as **Post-Quantum Cryptography (PQC)**.
The U.S. National Institute of Standards and Technology (NIST) has been leading a global standardization effort to select the most robust and efficient PQC algorithms. Lattice-based cryptography (like CRYSTALS-Dilithium) is emerging as a strong candidate to replace ECC.
Implementing PQC in Bitcoin requires a backward-compatible **hard fork**—a complex, community-wide effort similar to the deployment of SegWit or Taproot. This involves:
- Developing New Standards: Integrating the chosen NIST PQC standards into the Bitcoin protocol codebase.
- Protocol Upgrade: Enacting a soft or hard fork that allows new quantum-resistant addresses and transactions to be recognized and verified by the entire network.
- Migration Period: Users would then be required to move their funds from their current ECC addresses to the new PQC addresses within a specified timeframe to achieve complete quantum immunity.
This process is expected to take several years, but the groundwork is already being laid. By establishing a clear timeline and agreed-upon PQC standards now, developers ensure that the network will be ready long before CRQCs reach the required complexity.
The quantum threat is serious, but it is a race against time where the defenders have a significant head start. Bitcoin’s decentralized, iterative development model provides the necessary flexibility to adapt. By focusing on immediate risk mitigation (avoiding address reuse and utilizing modern formats) while simultaneously planning the long-term PQC transition, the community confirms that quantum vulnerability in Bitcoin is not an impending doom, but a challenge well within the scope of network governance and technological evolution.
Quantum Vulnerability in Bitcoin: A Manageable Risk
Quantum Vulnerability in Bitcoin: A Manageable Risk Wallpapers
Collection of quantum vulnerability in bitcoin: a manageable risk wallpapers for your desktop and mobile devices.

Dynamic Quantum Vulnerability In Bitcoin: A Manageable Risk View Illustration
This gorgeous quantum vulnerability in bitcoin: a manageable risk photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Detailed Quantum Vulnerability In Bitcoin: A Manageable Risk Capture Nature
Experience the crisp clarity of this stunning quantum vulnerability in bitcoin: a manageable risk image, available in high resolution for all your screens.

Mesmerizing Quantum Vulnerability In Bitcoin: A Manageable Risk Wallpaper for Your Screen
Explore this high-quality quantum vulnerability in bitcoin: a manageable risk image, perfect for enhancing your desktop or mobile wallpaper.

Dynamic Quantum Vulnerability In Bitcoin: A Manageable Risk View Collection
This gorgeous quantum vulnerability in bitcoin: a manageable risk photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Beautiful Quantum Vulnerability In Bitcoin: A Manageable Risk Wallpaper Collection
Discover an amazing quantum vulnerability in bitcoin: a manageable risk background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Vivid Quantum Vulnerability In Bitcoin: A Manageable Risk Picture for Desktop
Discover an amazing quantum vulnerability in bitcoin: a manageable risk background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Captivating Quantum Vulnerability In Bitcoin: A Manageable Risk Picture for Mobile
A captivating quantum vulnerability in bitcoin: a manageable risk scene that brings tranquility and beauty to any device.

Mesmerizing Quantum Vulnerability In Bitcoin: A Manageable Risk Background for Mobile
Experience the crisp clarity of this stunning quantum vulnerability in bitcoin: a manageable risk image, available in high resolution for all your screens.

Crisp Quantum Vulnerability In Bitcoin: A Manageable Risk Image for Desktop
Find inspiration with this unique quantum vulnerability in bitcoin: a manageable risk illustration, crafted to provide a fresh look for your background.

Detailed Quantum Vulnerability In Bitcoin: A Manageable Risk View Art
Transform your screen with this vivid quantum vulnerability in bitcoin: a manageable risk artwork, a true masterpiece of digital design.

Amazing Quantum Vulnerability In Bitcoin: A Manageable Risk Artwork Nature
Explore this high-quality quantum vulnerability in bitcoin: a manageable risk image, perfect for enhancing your desktop or mobile wallpaper.

Breathtaking Quantum Vulnerability In Bitcoin: A Manageable Risk Photo in HD
Discover an amazing quantum vulnerability in bitcoin: a manageable risk background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Vivid Quantum Vulnerability In Bitcoin: A Manageable Risk Landscape Digital Art
Transform your screen with this vivid quantum vulnerability in bitcoin: a manageable risk artwork, a true masterpiece of digital design.

Mesmerizing Quantum Vulnerability In Bitcoin: A Manageable Risk Artwork Collection
Explore this high-quality quantum vulnerability in bitcoin: a manageable risk image, perfect for enhancing your desktop or mobile wallpaper.
Amazing Quantum Vulnerability In Bitcoin: A Manageable Risk Wallpaper in HD
Discover an amazing quantum vulnerability in bitcoin: a manageable risk background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Lush Quantum Vulnerability In Bitcoin: A Manageable Risk View Illustration
A captivating quantum vulnerability in bitcoin: a manageable risk scene that brings tranquility and beauty to any device.
High-Quality Quantum Vulnerability In Bitcoin: A Manageable Risk Photo for Desktop
Explore this high-quality quantum vulnerability in bitcoin: a manageable risk image, perfect for enhancing your desktop or mobile wallpaper.

High-Quality Quantum Vulnerability In Bitcoin: A Manageable Risk Picture for Desktop
Experience the crisp clarity of this stunning quantum vulnerability in bitcoin: a manageable risk image, available in high resolution for all your screens.

Captivating Quantum Vulnerability In Bitcoin: A Manageable Risk Photo in 4K
Immerse yourself in the stunning details of this beautiful quantum vulnerability in bitcoin: a manageable risk wallpaper, designed for a captivating visual experience.

Exquisite Quantum Vulnerability In Bitcoin: A Manageable Risk Scene in 4K
Immerse yourself in the stunning details of this beautiful quantum vulnerability in bitcoin: a manageable risk wallpaper, designed for a captivating visual experience.
Download these quantum vulnerability in bitcoin: a manageable risk wallpapers for free and use them on your desktop or mobile devices.