How Can An Attacker Execute Malware Through A Script
How Can An Attacker Execute Malware Through A Script?
Ever wondered about the hidden dangers lurking in simple lines of code? If you're curious about how an attacker can execute malware through a script, you've come to the right place. It's a common, yet often underestimated, method cybercriminals use to slip nasty software onto your computer without you even realizing it. Let's break down this stealthy technique in an easy-to-understand way.
Understanding Scripts in Cyber Attacks
At its core, a script is just a series of commands executed by another program or operating system. Think of it as a mini-program designed to automate tasks. From updating your software to managing system processes, scripts are incredibly useful and a fundamental part of how computers work every day.
However, this very utility makes them a powerful weapon in the hands of an attacker. Instead of directly injecting a full malware executable, which is often easier for antivirus programs to detect, attackers can use scripts to perform malicious actions. These scripts can bypass traditional security measures, download further harmful components, or even directly manipulate your system.
Common Scripting Languages Used by Attackers
Cybercriminals often favor scripting languages that are natively supported by operating systems or widely available, reducing the need for additional software. This makes their attacks more seamless and harder to spot. Here are a few popular choices:
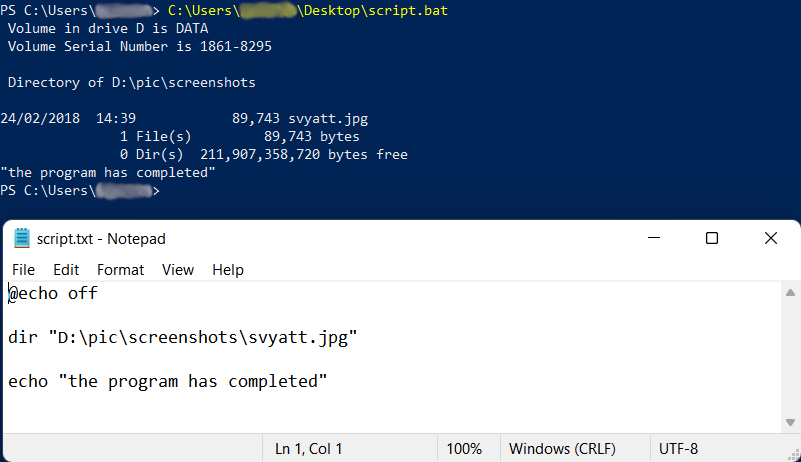
- PowerShell: A powerful command-line shell and scripting language developed by Microsoft. It's pre-installed on Windows systems, making it a prime target for attackers to execute commands, download files, and even run code directly from memory.
- JavaScript: Widely used for web development, JavaScript can be embedded in web pages or even in seemingly innocuous document files (like PDFs) to execute malicious code when opened.
- VBScript (Visual Basic Script): Another Microsoft scripting language, often seen in older office macros or in email attachments. Though less common than PowerShell now, it still poses a threat.
- Python: While a general-purpose programming language, Python scripts can also be used for malicious purposes, especially for creating backdoors or data exfiltration tools, often bundled within seemingly legitimate applications.
Delivery Methods: How Scripts Get Onto Your System
So, you know attackers use scripts. But how do these scripts actually land on your machine? The delivery methods are diverse, often relying on social engineering or exploiting software vulnerabilities.
- Phishing Emails: The classic. A malicious script can be an attachment (e.g., a macro-enabled Word document), or a link in the email can lead you to a website that automatically downloads or executes a script.
- Malicious Websites (Drive-by Downloads): Simply visiting a compromised website can trigger a script download or execution without your explicit consent. This often exploits vulnerabilities in your browser or plugins.
- Software Vulnerabilities: Attackers can find flaws in legitimate software to inject and execute their own scripts, gaining control over a part of your system.
- Infected USB Drives: Connecting a compromised USB drive can automatically run scripts configured to execute upon insertion, often leveraging Windows' AutoRun feature (though less common now due to security enhancements).
What Happens After Script Execution?
Once a malicious script successfully executes, the possibilities are grim. The script itself might not be the main malware; often, it acts as a 'downloader' or 'dropper' for the actual payload. It can be used to achieve various nefarious goals.
Common outcomes include downloading and installing ransomware, stealing sensitive data (passwords, banking info), creating backdoors for future access, or turning your computer into part of a botnet. Because scripts run within the context of legitimate programs, they can be harder for traditional antivirus to detect, as the malicious actions appear to originate from a trusted source.
Protecting Yourself from Script-Based Malware
Now that you understand how an attacker can execute malware through a script, you might be wondering how to stay safe. Prevention is key!
- Keep Your Software Updated: Regularly update your operating system, web browser, and all applications. Patches often fix vulnerabilities that attackers exploit.
- Use Reputable Antivirus/Antimalware: A good security suite can detect and block malicious scripts, especially those exhibiting suspicious behavior.
- Be Wary of Suspicious Emails & Links: Always double-check sender addresses and think twice before clicking on links or opening attachments from unknown sources.
- Enable a Firewall: A firewall helps control network traffic, blocking unauthorized connections that malicious scripts might try to establish.
- Disable Macros by Default: For programs like Microsoft Office, set macro security to high to prevent automatic execution of potentially harmful scripts. Only enable them for trusted documents.
- Educate Yourself: Knowledge is your best defense. Understanding the tactics helps you recognize threats before they become problems.
In conclusion, understanding how an attacker can execute malware through a script is crucial in today's digital landscape. Scripts offer a discreet yet powerful way for cybercriminals to compromise systems. By being vigilant, maintaining updated software, and employing robust security practices, you can significantly reduce your risk of falling victim to these subtle but dangerous attacks.
Frequently Asked Questions (FAQ)
- Q: Can antivirus software always stop script-based malware?
- A: While good antivirus software can detect and block many forms of script-based malware, especially those with known signatures or suspicious behavior, no solution is foolproof. Attackers constantly develop new obfuscation techniques to bypass detection. Layered security is always recommended.
- Q: Is PowerShell always dangerous?
- A: Absolutely not. PowerShell is a legitimate and incredibly powerful administrative tool for Windows systems. Its danger lies in how it's used. Just like a hammer can build a house or be used destructively, PowerShell's power can be leveraged for good or for malicious purposes.
- Q: What's the biggest risk with script malware compared to traditional executables?
- A: One of the biggest risks is their stealth and ease of execution. Since scripts often run within the context of legitimate applications or system processes, they can be harder to detect by traditional security measures that primarily look for known malicious executable files. They can also execute directly in memory without touching the disk, making forensic analysis more challenging.
How Can An Attacker Execute Malware Through A Script
How Can An Attacker Execute Malware Through A Script Wallpapers
Collection of how can an attacker execute malware through a script wallpapers for your desktop and mobile devices.

Mesmerizing How Can An Attacker Execute Malware Through A Script View Concept
Experience the crisp clarity of this stunning how can an attacker execute malware through a script image, available in high resolution for all your screens.

High-Quality How Can An Attacker Execute Malware Through A Script Photo Photography
Explore this high-quality how can an attacker execute malware through a script image, perfect for enhancing your desktop or mobile wallpaper.

Beautiful How Can An Attacker Execute Malware Through A Script Capture Digital Art
Experience the crisp clarity of this stunning how can an attacker execute malware through a script image, available in high resolution for all your screens.

Breathtaking How Can An Attacker Execute Malware Through A Script Landscape Nature
Transform your screen with this vivid how can an attacker execute malware through a script artwork, a true masterpiece of digital design.

Amazing How Can An Attacker Execute Malware Through A Script Design Digital Art
Transform your screen with this vivid how can an attacker execute malware through a script artwork, a true masterpiece of digital design.

Lush How Can An Attacker Execute Malware Through A Script Scene Concept
This gorgeous how can an attacker execute malware through a script photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Lush How Can An Attacker Execute Malware Through A Script Photo Digital Art
Find inspiration with this unique how can an attacker execute malware through a script illustration, crafted to provide a fresh look for your background.

Lush How Can An Attacker Execute Malware Through A Script Scene Digital Art
A captivating how can an attacker execute malware through a script scene that brings tranquility and beauty to any device.

Lush How Can An Attacker Execute Malware Through A Script Moment Art
This gorgeous how can an attacker execute malware through a script photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

High-Quality How Can An Attacker Execute Malware Through A Script Landscape Collection
Experience the crisp clarity of this stunning how can an attacker execute malware through a script image, available in high resolution for all your screens.

Detailed How Can An Attacker Execute Malware Through A Script Moment Collection
Transform your screen with this vivid how can an attacker execute malware through a script artwork, a true masterpiece of digital design.

Artistic How Can An Attacker Execute Malware Through A Script Design for Desktop
A captivating how can an attacker execute malware through a script scene that brings tranquility and beauty to any device.

Crisp How Can An Attacker Execute Malware Through A Script Photo Photography
Immerse yourself in the stunning details of this beautiful how can an attacker execute malware through a script wallpaper, designed for a captivating visual experience.

High-Quality How Can An Attacker Execute Malware Through A Script Design Collection
Discover an amazing how can an attacker execute malware through a script background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Gorgeous How Can An Attacker Execute Malware Through A Script Design in HD
This gorgeous how can an attacker execute malware through a script photo offers a breathtaking view, making it a perfect choice for your next wallpaper.
Stunning How Can An Attacker Execute Malware Through A Script Moment in 4K
A captivating how can an attacker execute malware through a script scene that brings tranquility and beauty to any device.

Vivid How Can An Attacker Execute Malware Through A Script Landscape in 4K
Discover an amazing how can an attacker execute malware through a script background image, ideal for personalizing your devices with vibrant colors and intricate designs.

Vibrant How Can An Attacker Execute Malware Through A Script Capture for Desktop
Experience the crisp clarity of this stunning how can an attacker execute malware through a script image, available in high resolution for all your screens.

Exquisite How Can An Attacker Execute Malware Through A Script Image Collection
This gorgeous how can an attacker execute malware through a script photo offers a breathtaking view, making it a perfect choice for your next wallpaper.

Gorgeous How Can An Attacker Execute Malware Through A Script Artwork for Desktop
Find inspiration with this unique how can an attacker execute malware through a script illustration, crafted to provide a fresh look for your background.
Download these how can an attacker execute malware through a script wallpapers for free and use them on your desktop or mobile devices.